What is the simplest malware in the world?
During a malware analysis class I taught recently, one of the students asked me what was “the simplest malware in the world”. Of course, the answer to this question would depend heavily on one’s definitions of ‘simplest’ and ‘malware’, as well as on a target hardware architecture and its operating system (and potentially additional software and other factors), but I thought that it was conceptually interesting enough to devote today's diary to.
If we were to discuss simplicity only in the terms of overall size of the code, and define ‘malware’ (with small help from NIST[1]), as a “program, that is intended to compromise the confidentiality, integrity, or availability of the victim’s data, applications, or operating system or to otherwise annoy or hinder the victim”, then the simplest malware overall would probably be a single instruction of the “Halt and Catch Fire” type[2] for any platform, on which instructions capable (by design or due to a bug) of stopping CPU operations were available and could be executed on their own. Or – to be exact – the simplest malware would probably be such a code on a platform, on which the instruction would be shortest (which would probably come to a single byte). However, this is purely theoretical answer from a historical standpoint.
If we were move beyond this case and focus only on code that can run on modern operating systems and current hardware platforms, the situation becomes much more complex. And although I spent some time thinking about what the smallest malware might be, and I do have a potential answer, I’m not completely certain it is the correct one. If you can think of a smaller example of a working malicious code, let us know in the comments.
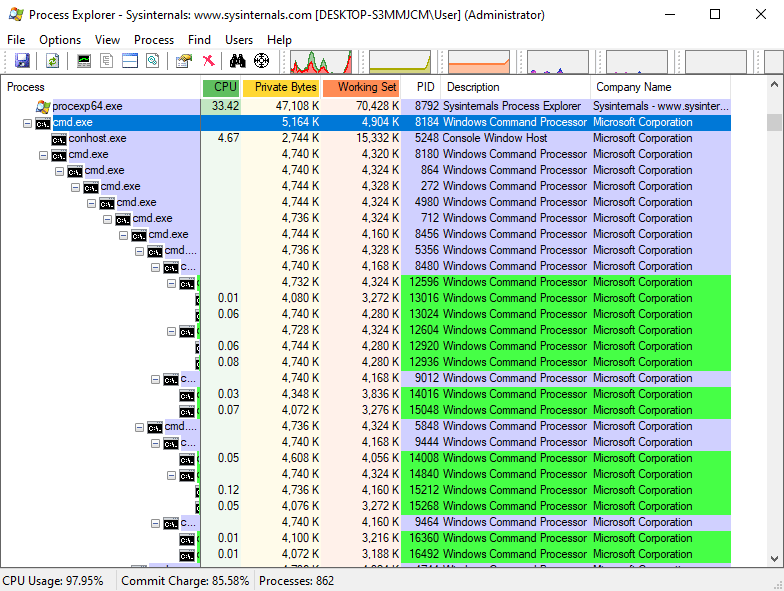
Anyway, since I wasn’t able to think of, nor find anything “smaller”, I came to believe that the most common version of the fork bomb for Windows might be the smallest (at least the smallest current) real world malware.
Fork bombs, or “rabbits” or “wabbits”, as they are also sometimes called, are probably among the oldest types of malware overall[3], and they are quite simple. Their only function is to execute two copies of themselves each time they are run. This means that once a fork bomb is executed on a system, the number of fork bomb processes running on that system will start exponentially increasing, which – as you can probably imagine – will quickly result in resource exhaustion.
The most well-known fork bomb for Windows, which may be implemented as a standalone batch file, is made up of only the following 5 ASCII characters (i.e., 5 bytes).
%0|%0
Despite its small size, it can have a quick and fairly unpleasant effect – feel free to test it for yourself (though, I would recommend that you do so in a VM, which you won’t mind rebooting afterwards).
As I’ve mentioned, I’m not completely sure that this fork bomb is the smallest malware there is for modern platforms, however, with only 5 bytes in length, it has to be at least close... And it shows quite well that malware does not have to be complex to be effective.
[1] https://csrc.nist.gov/glossary/term/malware
[2] https://en.wikipedia.org/wiki/Halt_and_Catch_Fire_(computing)
[3] https://en.wikipedia.org/wiki/Wabbit_(computing)
-----------
Jan Kopriva
@jk0pr
Nettles Consulting



Comments